Slingcode Is Out
2020-07-17At the end of June I finally shipped Slingcode, the browser based code editor I've
![]()
Hello, I'm Chris. I'm researching and implementing decentralized technologies.
Here you can find software & hardware I'm working on, and posts I've written on the topic. I'm interested in technology that enables people to control their own data, freedom of expression, web based decentralization, and trust minimised architectures.
At the end of June I finally shipped Slingcode, the browser based code editor I've
Recently I was teaching one of my kids a bit of web coding. This is way more complicated than it should be. There are so many moving parts - configuration, build systems, editors, hosting requirements, certificates etc. just to get a simple web app running. Why?
I thought back to when I was learning to code with my mother on our Apple IIe. The computer was ours. The code was ours. The data was ours.
Photographs are easy to fake. So much so that there is a turn of phrase to describe it. People say something is "'shopped" when they are skeptical regarding the veracity of an image. This refers to the image editing program Photoshop which is often used to modify images. For example the magazine industry routinely modifies the photographs which appear in their pages.

A few weeks ago at the BSides Perth conference I announced this piece of hardware I've been tinkering on.
I've got three conference talks coming up in Perth (Australia), London, and The Gold Coast (Australia). If you're nearby let me know - I would love to buy you a coffee/beer and hear what you're up to.
In November 2015 Nick Szabo gave a talk on the history of the blockchain which was dense with useful ideas.

In 2014 Arvid Norberg and Steven Siloti came up with a BitTorrent extension called BEP44. The basic purpose of BEP44 is to allow people to store small pieces of information in a part of the BitTorrent network called the DHT. The DHT ("distributed hash table") is a key/value lookup table that is highly decentralized. Prior to BEP44 it was used to look up the IP addresses of peers from the hashes of the torrent they were sharing.
This post originally appeared on the David Walsh blog.
In this 15 minute tutorial we're going to build a simple decentralized chat application which runs entirely in a web browser.
Hashcash is a mechanism for defending against spam and denial-of-service attacks in email and other decentralized systems. Implementors of systems using hashcash face the issue of how to set the proof-of-work difficulty. A general solution to this problem is given which can be used to predictably allocate resources in decentralized systems where individual nodes each contribute finite resources. Some emergent effects of this solution are explored.
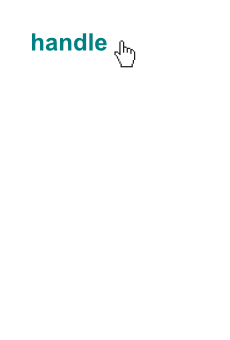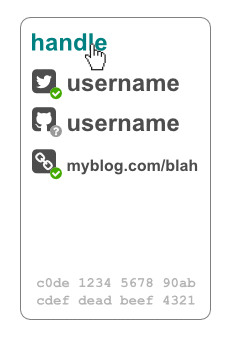
A problem faced by decentralized systems is that of naming things. The problem is best expressed by Zooko's Triangle which conjectured that no single kind of naming system can provide names satisfying all three of the following properties:
Web applications often follow a client-server model meaning that there is a piece of software which runs in your web browser (the client) and a piece of software which runs on a server somewhere. I'm interested in this model, where it came from, and where it's going, and I discuss this below. I'll also discuss a new model for self-hosting web applications that I've been exploring.
Here are some illustrated explanations of the main ways in which cryptographic hash functions can be attacked, and be resistant to those attacks.
Zooko Wilcox's blog post Lessons From The History Of Attacks On Secure Hash Functions gives us a nice overview of these and I've quoted his concise explanations below. Check out his great post for more detail and history on this topic.
I built a little blockchain-in-a-browser in ClojureScript to help understand the underlying algorithms.
You can simulate a network of peers by opening multiple browser tabs. Each peer can mine blocks and make transactions independently and the resulting blockchain will resolve conflicts correctly across all tabs.

This is a Hexadecimal die that you can 3d print. Download the STL file or get the source code on GitHub. Hopefully useful when generating private keys and the like.